Auto ID
Access Control With RFID
Chris Randle // Vice President of Industry Solutions // ELATEC Inc. // Palm City, FL
With automation systems becoming increasingly interconnected, limiting access to controllers and HMI software is crucial. Photo courtesy ELATEC Inc.
Chris Randle // Vice President of Industry Solutions // ELATEC Inc. // Palm City, FL
Auto ID
With automation systems becoming increasingly interconnected, limiting access to controllers and HMI software is crucial. Photo courtesy ELATEC Inc.
Access Control With RFID
RFID technology can help manufacturers control access to critical hardware and software.
What’s the best way to ensure product quality and production uptime in industrial automation? Make sure that only trained and authorized people can access the programmable controllers.
A typical assembly plant is equipped with an assortment of machinery and robots to fabricate and assemble various products. These machines are often driven by programmable controllers (PLCs or industrial PCs) and use a human-machine interface (HMI) for configuration, notifications and routine control. The controllers have software that perform specific tasks in a logical order to drive the machine or process. With automation systems growing in number and increasingly interconnected, limiting access to controllers and HMI software is crucial.
Automation controllers are usually connected through plantwide Ethernet networks to IT servers that include databases for collecting information to manage things like employee identity and authorization to run and support plant manufacturing processes. The names of plant personnel who are authorized to change or update controller and HMI software are stored on IT servers. The data lists whether employees have the proper skill sets and whether they are trained and certified to access the manufacturing system hardware and software. It also shows whether employees are authorized to enter a hazardous area to perform maintenance or other activities.
Plant IT servers typically store copies of the controller and HMI software for backup, change control and disaster recovery purposes. To prevent unauthorized software updates, a user authentication system should be installed on or near the operator station, requiring the physical presence of the person authorized to update or change the software. This added authentication and authorization requirement protects the manufacturing system, engineers, machine operators and maintenance personnel.

To prevent unauthorized software updates, a user authentication system should be installed on or near the operator station, requiring the physical presence of the person authorized to update or change the software. Photo courtesy ELATEC Inc.
Controlling Access
Working with the IT department, plant control engineers are usually responsible for authorization to access controller and HMI software. Authorized personnel typically include plant engineers, maintenance electricians and IT personnel who can access software running specific processes. The level of access varies according to the individual’s function in the plant. Engineers usually have full access to upload, download and change controller and HMI software. IT personnel are usually only able to upload or download software for backup and disaster recovery purposes. Plant maintenance electricians typically have limited access to change software and only for process troubleshooting. The specific authorization may vary from plant to plant, but identification of who accessed the software, who made changes and when is logged in a database to track changes for review when necessary.
There are many reasons for engineers to implement systems that log and track software changes to controllers and HMIs. The primary reason is that unauthorized changes can cause serious harm, including long startup times, downtime, quality problems, unsafe operating conditions, and software losses. In addition, engineers, operators and maintenance personnel on different shifts may be unaware of changes, who made them, or when.
For authentication and authorization systems to work, they must be easy to use, flexible, durable, secure, and stand up well to environmental elements. Radio frequency identification (RFID) technology addresses these requirements better than magnetic stripe cards, chip cards and PIN pads. RFID cards are the most widely used form of authentication and access control today.
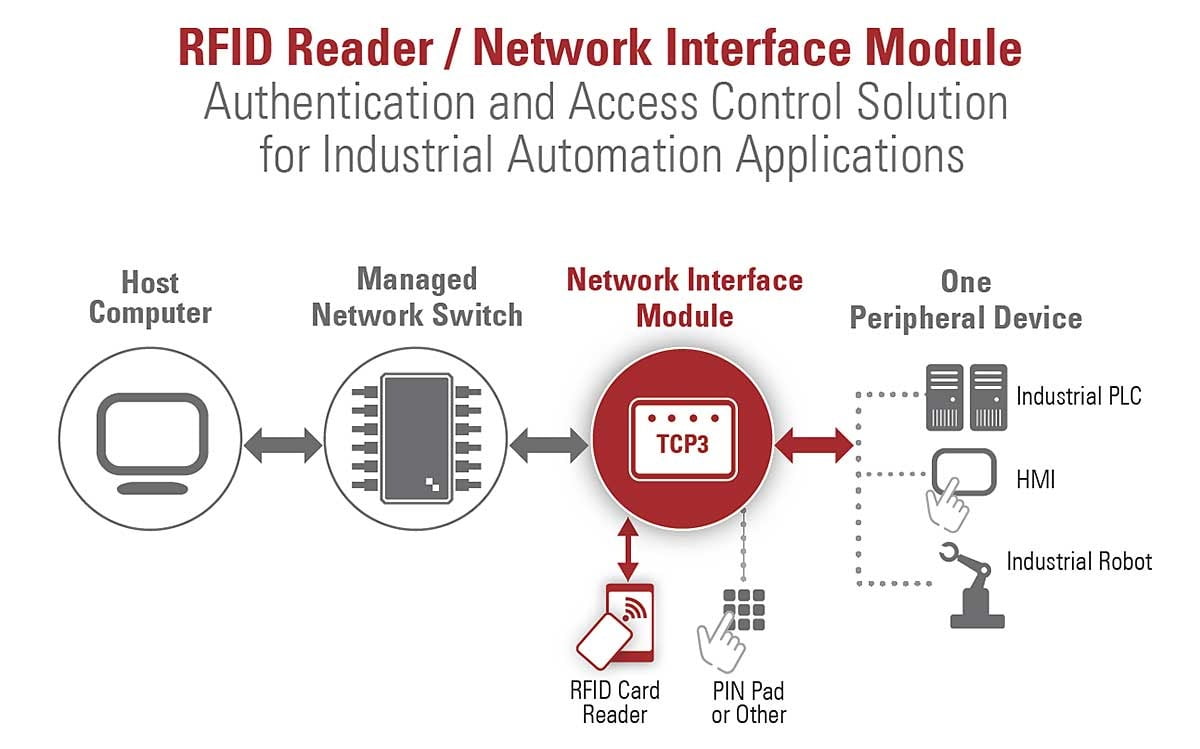
This diagram shows a system for authentication and access control of industrial automation software using an RFID reader combined with a network interface module. Illustration courtesy ELATEC Inc.
One of the benefits of RFID authentication and access control is that it is easy and convenient for users. RFID cards are touchless; the user only has to wave the card within a few inches of the reader to be read.
RFID readers can be implemented throughout a factory for multipurpose authentication using existing employee building-entry ID cards. Functionality such as time-based access control, access to manufacturing processes, access to controller and HMI software and hazardous areas can be added. Additionally, RFID readers can often read and write to more than one type of card. Should plant requirements change, cards can be updated without issuing a new card.
When connected to plantwide networks, readers can use various protocols, such as gigabit Ethernet, to communicate with IT systems and automation applications like programmable controllers, HMIs and robots.
Since they are touchless, both cards and readers experience less wear and tear than in systems requiring the card to contact the reader, such as in magnetic stripe cards and chip card systems. Over time, this can minimize the replacement cost of both cards and readers.
RFID card systems are more secure than other card-based identification technologies. Data transfer between cards and readers and message traffic between card readers and plant networks can be encrypted.
RFID readers and cards can also execute a kill command if the card is lost or stolen. Since the kill command deactivates the card, it prevents unauthorized access to sensitive data, hardware and software that controls industrial manufacturing processes and hazardous areas in the plant.
Finally, given industrial settings, RFID cards and readers are more durable in harsh plant floor environments. They resist dust, heat, dirt and general wear and tear better than other authentication and access control technologies.
RFID is a secure, flexible, reliable, and easy-to-use technology for authentication and access control of industrial hardware and software. There are multiple RFID reader technologies on the market, but they are not all created equal. Choosing a comprehensive platform that offers a wide range of options can help your organization implement a system that will meet your needs now and in the future.

RFID cards are touchless; the user only has to wave the card within a few inches of the reader to be read. Photo courtesy ELATEC Inc.
ASSEMBLY ONLINE
For more information on RFID technology, visit www.assemblymag.com to read these articles:



